Security engineered for the next decade.
Security engineered for the next decade.
Security engineered
for the next decade.


Trusted by 100+ top companies, investors, and entrepreneurs


FINANCIAL CYBERSECURITY
Secure financial systems in real time
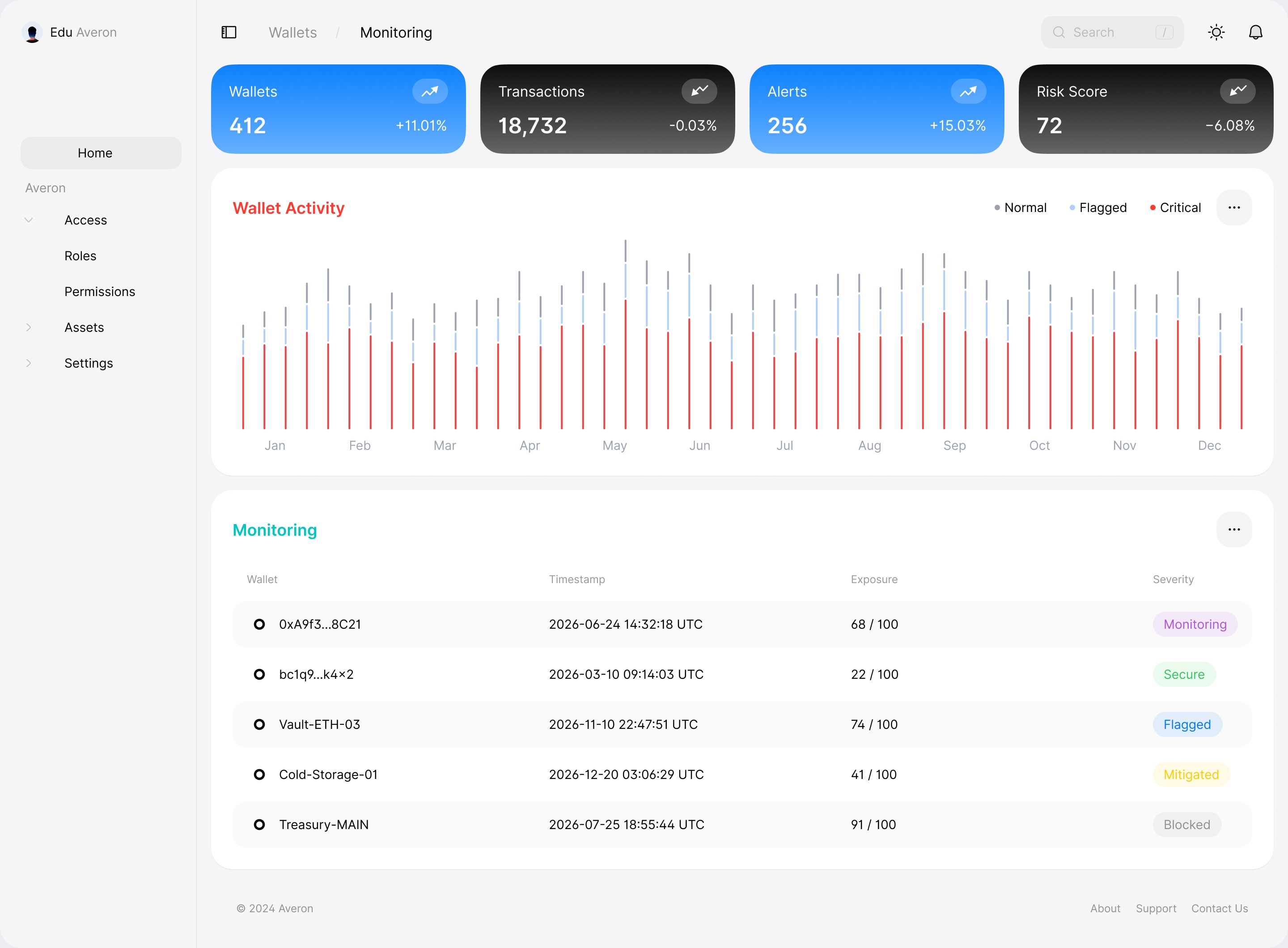
A unified view of your financial infrastructure, including hot and cold wallets, continuously monitored by Averon AI to detect threats, predict risk, and activate a security layer before critical operations are compromised.
Threat Monitoring
Threat Monitoring
Active Defense
Active Defense
Compliance Insights
Compliance Insights
Risk Prediction
Risk Prediction

FINANCIAL CYBERSECURITY
Secure financial systems in real time
A unified view of your financial infrastructure, including hot and cold wallets, continuously monitored by Averon AI to detect threats, predict risk, and activate a security layer before critical operations are compromised.
Threat Monitoring
Active Defense
Compliance Insights
Risk Prediction
financial management
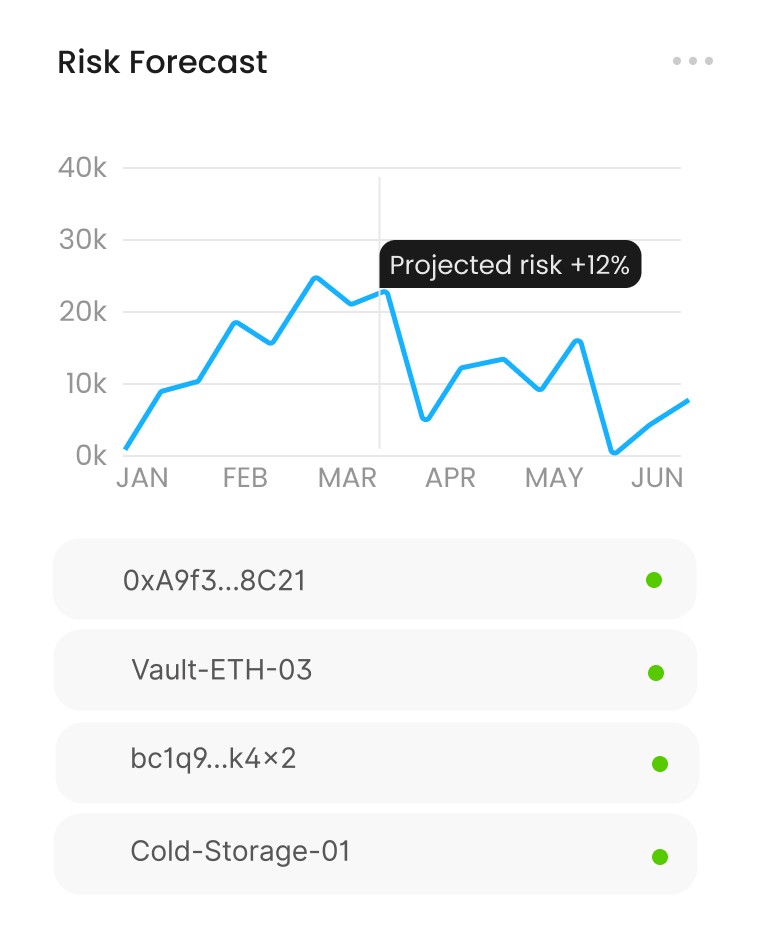
Detect risk. Protect capital.
Averon analyzes financial activity in real time, identifying anomalies, predicting attack vectors, and reinforcing systems before damage occurs.
Transaction Shield
Transaction Shield
AI Forecasting
AI Forecasting
Anomaly Detection
Anomaly Detection
Secure Integrations
Secure Integrations

financial management
Detect risk, protect capital.
Averon analyzes financial activity in real time, identifying anomalies, predicting attack vectors, and reinforcing systems before damage occurs.
Transaction Shield
AI Forecasting
Anomaly Detection
Secure Integrations

features
Built for financial infrastructure, powered by AI
Built for financial infrastructure, powered by AI
Intelligent, flexible, and built for your infrastructure


Averon adapts to your systems, workflows, and security policies configuring its AI layer to match how your financial operations actually run, not the other way around.
Meet Layla, Averon’s AI powered security operator

Layla is Averon’s AI security operator designed to analyze wallet activity, evaluate risk signals, and surface potential threats. Layla helps your team understand risk in context and take action in real time across security operations.
Integrates seamlessly with your infrastructure
Averon connects directly to your financial systems, APIs, and security stack enabling real time monitoring, automated responses, and unified risk intelligence across your operations.
Meet Layla
Layla is Averon’s AI powered security operator, designed to analyze threats, explain risk, and assist your team with real time intelligence and actions.
Meet Layla
Layla is Averon’s AI powered security operator, designed to analyze threats, explain risk, and assist your team with real time intelligence and actions.
See
Visualize threats, exposure, and system health across multiple perspectives giving your team full situational awareness to act with precision.
See
Visualize threats, exposure, and system health across multiple perspectives giving your team full situational awareness to act with precision.
Simulates
Averon runs continuous AI driven attack simulations against your financial infrastructure, revealing how systems would fail and where defenses must be reinforced before real attackers try.
Simulates
Averon runs continuous AI driven attack simulations against your financial infrastructure, revealing how systems would fail and where defenses must be reinforced before real attackers try.
Monitoring
Averon continuously monitors hot and cold wallets through on chain observation and behavioral risk modeling, detecting anomalies and estimating threat probability to trigger preventive security measures before execution.
Monitoring
Averon continuously monitors hot and cold wallets through on chain observation and behavioral risk modeling, detecting anomalies and estimating threat probability to trigger preventive security measures before execution.
Monitoring
Averon continuously monitors hot and cold wallets through on chain observation and behavioral risk modeling, detecting anomalies and estimating threat probability to trigger preventive security measures before execution.
features
Built for financial infrastructure powered by AI
Intelligent, flexible, and built for your infrastructure

Averon adapts to your systems, workflows, and security policies configuring its AI layer to match how your financial operations actually run, not the other way around.
Meet Layla, Averon’s AI powered security operator

Layla is Averon’s AI security operator designed to analyze wallet activity, evaluate risk signals, and surface potential threats. Layla helps your team understand risk in context and take action in real time across security operations.
Integrates seamlessly with your infrastructure
Averon connects directly to your financial systems, APIs, and security stack enabling real time monitoring, automated responses, and unified risk intelligence across your operations.
Meet Layla
Layla is Averon’s AI powered security operator, designed to analyze threats, explain risk, and assist your team with real time intelligence and actions.
See
Visualize threats, exposure, and system health across multiple perspectives giving your team full situational awareness to act with precision.
Simulates
Averon runs continuous AI driven attack simulations against your financial infrastructure, revealing how systems would fail and where defenses must be reinforced before real attackers try.
Monitoring
Averon continuously monitors hot and cold wallets through on chain observation and behavioral risk modeling, detecting anomalies and estimating threat probability to trigger preventive security measures before execution.
Monitoring
Averon continuously monitors hot and cold wallets through on chain observation and behavioral risk modeling, detecting anomalies and estimating threat probability to trigger preventive security measures before execution.
“Averon exists to redefine what financial security can be.”
Daniel Vega, Thomas Samper
Founders
“Averon exists to redefine what financial security can be.”
Daniel Vega, Thomas Samper
Founders
“Doesn’t just alert us to threats it explains them. For the first time, our security team understands risk in business terms, not just technical noise.”
Head of Security
Fintech Company
“Averon surprised us with its attack simulation. Seeing how our systems could fail before anything happened.”
Chief Risk Officer
Financial Services Firm
“It feels like a command platform, not a tool. It helped us move from reactive security to proactive defense.”
VP of Engineering
Global Fintech
“It shifted our security strategy from monitoring events to understanding impact. Decisions that used to take hours now take minutes.”
CTO
Digital Payments Platform
“Doesn’t just alert us to threats it explains them. For the first time, our security team understands risk in business terms, not just technical noise.”
Head of Security
Fintech Company
“It feels like a command platform, not a tool. It helped us move from reactive security to proactive defense.”
VP of Engineering
Global Fintech
“Averon surprised us with its attack simulation. Seeing how our systems could fail before anything happened completely changed how we approach security.”
Chief Risk Officer
Financial Services Firm
“It shifted our security strategy from monitoring events to understanding impact. Decisions that used to take hours now take minutes.”
CTO
Digital Payments Platform
“Averon exists to redefine what financial security can be.”
Daniel Vega, Thomas Samper
Founders
“Doesn’t just alert us to threats it explains them. For the first time, our security team understands risk in business terms, not just technical noise.”
Head of Security
Fintech Company
“Averon surprised us with its attack simulation. Seeing how our systems could fail before anything happened.”
Chief Risk Officer
Financial Services Firm
“It feels like a command platform, not a tool. It helped us move from reactive security to proactive defense.”
VP of Engineering
Global Fintech
“It shifted our security strategy from monitoring events to understanding impact. Decisions that used to take hours now take minutes.”
CTO
Digital Payments Platform
“Doesn’t just alert us to threats it explains them. For the first time, our security team understands risk in business terms, not just technical noise.”
Head of Security
Fintech Company
“It feels like a command platform, not a tool. It helped us move from reactive security to proactive defense.”
VP of Engineering
Global Fintech
“Averon surprised us with its attack simulation. Seeing how our systems could fail before anything happened completely changed how we approach security.”
Chief Risk Officer
Financial Services Firm
“It shifted our security strategy from monitoring events to understanding impact. Decisions that used to take hours now take minutes.”
CTO
Digital Payments Platform
pricing
Simple plans
for critical security
Averon Core
For growing financial teams.
Real time threat monitoring
AI driven risk analysis
Transaction & infrastructure protection
Standard integrations
Security analytics dashboard
Averon Enterprises
For companies that take care of their infrastructure
Everything in Averon Core
Continuous attack simulation
Active defense automation
Advanced compliance intelligence
Dedicated security onboarding
Averon Core
For growing financial teams.
Real time threat monitoring
AI driven risk analysis
Transaction & infrastructure protection
Standard integrations
Security analytics dashboard
Averon Enterprises
For companies that take care of their infrastructure
Everything in Averon Core
Continuous attack simulation
Active defense automation
Advanced compliance intelligence
Dedicated security onboarding
How Averon is deployed
How Averon is deployed
2. Assessment
Averon activates read-only monitoring across hot and cold wallets, learning normal behavior patterns and calibrating risk models to your infrastructure.
2. Assessment
Averon activates read-only monitoring across hot and cold wallets, learning normal behavior patterns and calibrating risk models to your infrastructure.
1. Onboarding
After purchase, Averon works with your team to map wallets, workflows, and risk policies, defining monitoring scope and thresholds without key access or fund custody.
1. Onboarding
After purchase, Averon works with your team to map wallets, workflows, and risk policies, defining monitoring scope and thresholds without key access or fund custody.
3. Response
Averon surfaces risk signals and threat probability in real time, enabling pre-emptive action through alerts, policies, and approvals before execution.
3. Response
Averon surfaces risk signals and threat probability in real time, enabling pre-emptive action through alerts, policies, and approvals before execution.
pricing
Simple plans
for critical security
Averon Core
For growing financial teams.
Real time threat monitoring
AI driven risk analysis
Transaction & infrastructure protection
Standard integrations
Security analytics dashboard
Averon Enterprises
For companies that take care of their infrastructure
Everything in Averon Core
Continuous attack simulation
Active defense automation
Advanced compliance intelligence
Dedicated security onboarding
How Averon is deployed
2. Assessment
Averon activates read-only monitoring across hot and cold wallets, learning normal behavior patterns and calibrating risk models to your infrastructure.
1. Onboarding
After purchase, Averon works with your team to map wallets, workflows, and risk policies, defining monitoring scope and thresholds without key access or fund custody.
3. Response
Averon surfaces risk signals and threat probability in real time, enabling pre-emptive action through alerts, policies, and approvals before execution.
How Averon is deployed
1. Onboarding
After purchase, Averon works with your team to map wallets, workflows, and risk policies, defining monitoring scope and thresholds without key access or fund custody.
1. Onboarding
After purchase, Averon works with your team to map wallets, workflows, and risk policies, defining monitoring scope and thresholds without key access or fund custody.
2. Assessment
Averon activates read-only monitoring across hot and cold wallets, learning normal behavior patterns and calibrating risk models to your infrastructure.
2. Assessment
Averon activates read-only monitoring across hot and cold wallets, learning normal behavior patterns and calibrating risk models to your infrastructure.
3. Response
Averon surfaces risk signals and threat probability in real time, enabling pre-emptive action through alerts, policies, and approvals before execution.
3. Response
Averon surfaces risk signals and threat probability in real time, enabling pre-emptive action through alerts, policies, and approvals before execution.















